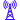Smarter Fraud Prevention with AI-Driven Decisioning
Fraud threats are constantly evolving, and static, rule-based detection systems are no longer enough. Balancing strong fraud prevention with a seamless customer experience is critical to minimizing losses and maximizing growth.
GDS Link’s fraud mitigation solutions leverage AI, machine learning, and real-time data orchestration to detect suspicious activity before losses occur—without unnecessary friction for genuine customers.
Prevent fraud losses and reduce friction with GDS Link
Prevent fraud before it happens
Real-Time Risk Detection: Instantly flag suspicious transactions using AI-powered analytics.
Multi-Layered Fraud Prevention: Combine device intelligence, behavioral biometrics, and transaction monitoring for enhanced accuracy.
Adaptive Risk-Based Authentication: Dynamically adjust security protocols to minimize user friction.
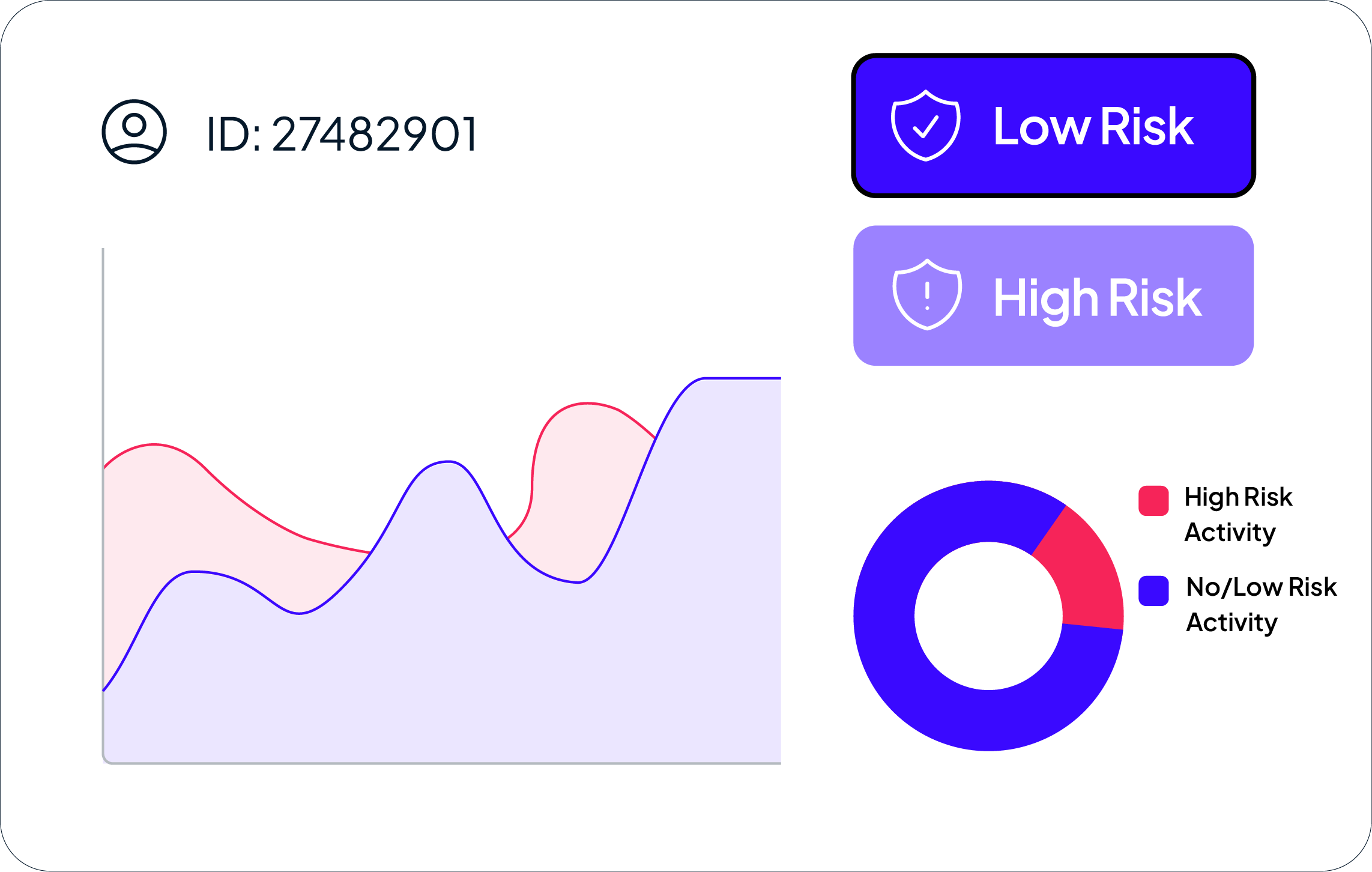
Reduce false positives and improve customer experience
AI-Powered Identity Verification: Detect synthetic identities and prevent fraud without unnecessary delays.
Behavioral Fraud Analysis: Monitor user patterns to differentiate genuine customers from fraudsters.
Risk-Based Authentication: Apply extra security only when necessary, ensuring seamless customer interactions.
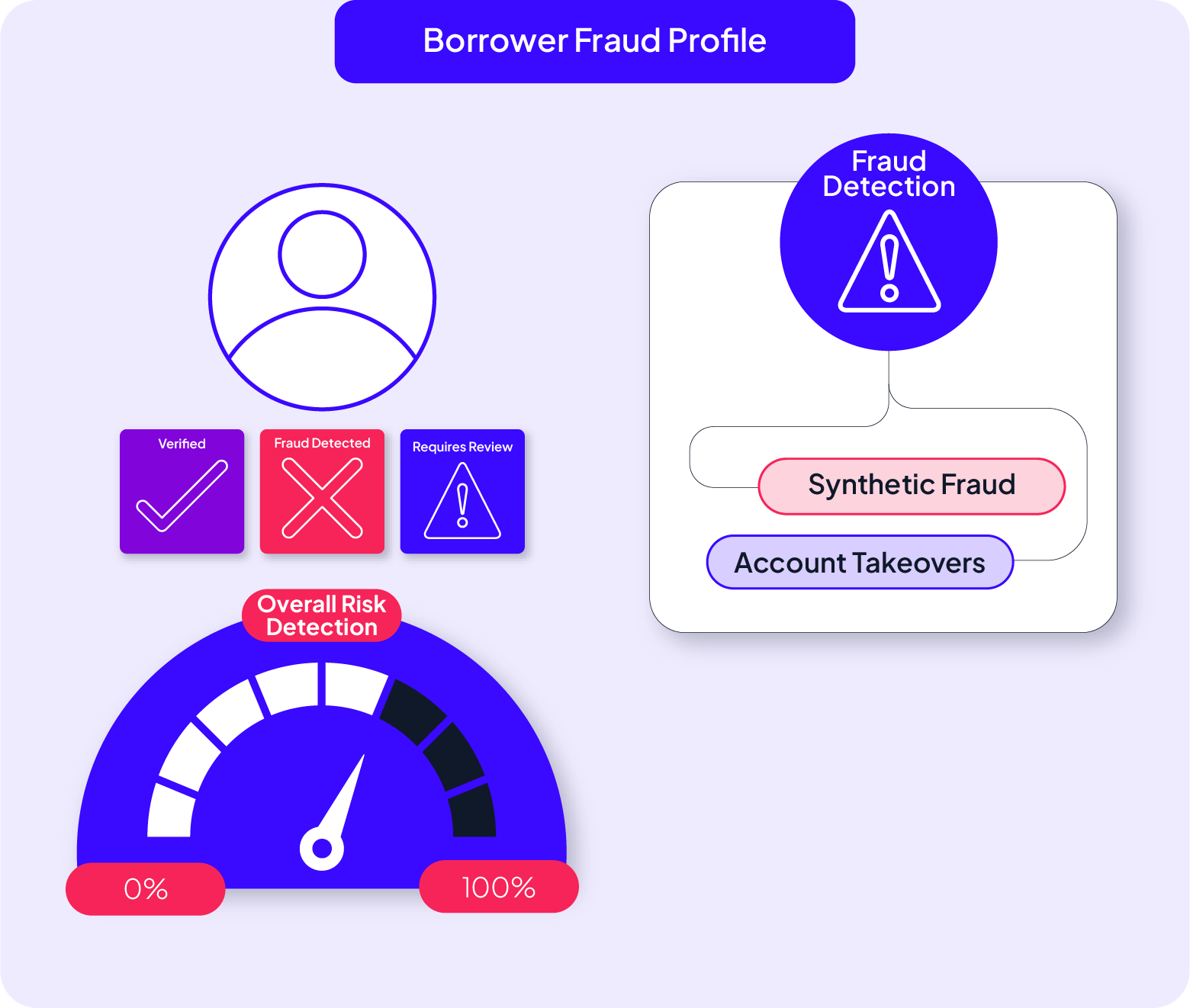
Automate investigations and strengthen fraud strategies
Integrated Case Management: Automate fraud investigations and track flagged transactions from detection to resolution.
Configurable No-Code Workflows: Adapt fraud detection models without IT bottlenecks.
Continuous AI Model Optimization: Improve fraud detection accuracy with ongoing risk assessments.
Why GDS Link outperforms other fraud prevention solutions
Detect and prevent fraud in real time with machine learning, behavioral intelligence, and layered risk analysis, giving you deeper insights and stronger protection against evolving threats.
Unlike vendor-restricted solutions, GDS Link gives lenders the flexibility to adjust fraud rules and response strategies in real time, ensuring they stay ahead of emerging threats.
Reduce false positives and eliminate unnecessary authentication steps while improving approval rates for legitimate customers, creating a smoother and more efficient experience.
"With GDS Link, we’ve automated 65% of our decisions, more than tripled our revenue over five years, and gained the tools to grow even faster while improving accuracy and reducing fraud. GDS Link has been instrumental in our success."
Own your strategy, seize every opportunity
Stop fraud before it happens, reduce false positives, and approve more genuine customers with AI-powered fraud mitigation. Contact us to learn how our solutions can strengthen your fraud mitigation strategies.